Students can Download Computer Applications Chapter 9 Introduction to Internet and Email Questions and Answers, Notes Pdf, Samacheer Kalvi 11th Computer Applications Book Solutions Guide Pdf helps you to revise the complete Tamilnadu State Board New Syllabus and score more marks in your examinations.
Tamilnadu Samacheer Kalvi 11th Computer Applications Solutions Chapter 9 Introduction to Internet and Email
Samacheer Kalvi 11th Computer Applications Introduction to Internet and Email Text Book Back Questions and Answers
I. Choose The Correct Answer
Question 1.
What is the expansion of WLAN?
(a) Wireless Local Area Network
(b) Wired Local Area Network
(c) Wireless Local Area Netware
(d) Wireless Area Netbande
Answer:
(a) Wireless Local Area Network
![]()
Question 2.
Range of Campus Network is:
(a) 10 KM
(b) 5 KM
(c) 25 KM
(d) 20 KM
Answer:
(b) 5 KM
Question 3.
Each computer on net is called:
(a) host
(b) server
(c) workstation
(d) node
Answer:
(a) host
![]()
Question 4.
The Internet is governed by:
(a) ICANM
(b) ICANN
(c) ICMA
(d) ICNNA
Answer:
(b) ICANN
Question 5.
Expansion of W3C:
(a) World Wide Web Consortium
(b) Wide World Web Consortium
(c) World Web Wide Consortium
(d) World Wide Web Consortium
Answer:
(a) World Wide Web Consortium
![]()
Question 6.
W3C was established in 1994 by:
(a) Tim Berners-Lee
(b) Tim Bumard-Lee
(c) Kim Berners
(d) Kim Bernard-Lee
Answer:
(a) Tim Berners-Lee
Question 7.
Hotspot uses which type of network services?
(a) LAN
(b) PAN
(c) WLAN
(d) CAN
Answer:
(c) WLAN
![]()
Question 8.
USB WiFi adapters are often called as:
(a) data card
(b) pen drive
(c) dongles
(d) memory card
Answer:
(c) dongles
Question 9.
Looking for information on the Internet is called:
(a) surfing
(b) searching
(c) finding
(d) glancing
Answer:
(a) surfing
![]()
Question 10.
Safari web browser was developed by:
(a) Google
(b) Apple
(c) Microsoft
(d) Linux Corpn
Answer:
(b) Apple
Question 11.
How many types of websites are available?
(a) 3
(b) 2
(c) 4
(d) 6
Answer:
(b) 2
II. Answer To The Following Questions
Question 1.
List any four types of available networks. Depending upon geographical area covered by a network, it is classified as:
Answer:
- Local Area Network (LAN)
- Metropolitan Area Network (MAN)
- Wide Area Network (WAN)
- Personal Area Network (PAN)
- Campus Area Network (CAN)
- Wireless Local Area Network (W-LAN)
![]()
Question 2.
Name the two important protocols for Internet?
Answer:
The Internet is a globally connected network system that uses TCP/IP (Transmission Control Protocol/Intemet Protocol) to transmit data via various types of media.
Question 3.
What is a network?
Answer:
A network is a collection of interconnected devices. (Eg: Computers, printers, etc…).
![]()
Question 4.
What is the role of ICANN ?
Answer:
Internet Corporation for Assigned Names and Numbers (ICANN) administers the domain name registration. It helps to avoid a name which is already registered.
Question 5.
What is a search engine?
Answer:
A search engine is a software system that is designed to search for information on the World Wide Web.
Eg: Yahoo, Lycos, Altavista, Hotbot, Google and Askjeeves.
![]()
Question 6.
What is a browser?
Answer:
A web browser is a software application for accessing information on the World-Wide Web. Eg: Internet Explorer, Chrome, Firefox, etc…
Question 7.
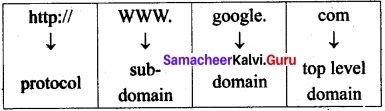
What are the components of url addressing?
Answer:
- Protocol
- Sub-domain
- Domain
- Top level domain.
Eg:
Question 8.
What is a website?
Answer:
A website is a collection of webpages.
Eg: If there is a company that owns sricompany. com then this Website will have several Webpages like Home, About Us, Contact Us, Testimonials, Products, Services, FAQ’s and others.
![]()
Question 9.
What is CC and BCC in an email?
Answer:
The CC (Carbon Copy) field allows you to specify recipients who are not direct addressees (listed in the “To” field). This field is optional. The BCC (Blind Carbon Copy) field is similar to CC, except the recipients are secret. Each BCC recipient will receive the e-mail, but will not see who else received a copy.
Question 10.
What is a Static Web Page?
Answer:
Web pages are called Static websites as they remain the same whenever it is visited. Examples of static Websites are website owned by Small business organizations, School websites etc…
![]()
Question 11.
What is a Dynamic Web Page?
Answer:
Websites that displays marks of Public Examinations and Entrance Examinations changes when different register numbers are given. Such websites are called as Dynamic Websites.
Eg: Websites of Government and Entrance Exams.
Question 12.
What are the benefits of e-governance?
Answer:
- Reduced corruption,
- High transparency,
- Increased convenience,
- Reduction in overall cost,
- Expanded reach of government.
![]()
Question 13.
What is Phishing?
Answer:
Phishing scams are fraudulent attempts by cyber criminals to obtain private information. Phishing scams often appear in the guise of email messages designed to appear as though they are from legitimate sources. For example, the message would try to lure you into giving your personal information by pretending that your bank.
III. Answer To The Following Questions
Question 1.
Differentiate PAN and CAN network?
Answer:
PAN:
- Personal Area Network, its ranges upto 100 meters.
- Speed upto 250 Kbps.
- Hotspot may connect upto 8 devices.
CAN:
- Campus Area Network, its range upto 5 km.
- Speed upto 40 Kb/s to 1 MB/s.
- High Bandwdith Multi- departmental Network access.
Question 2.
What is TCP/IP?
Answer:
The Internet uses TCP/IP (Transmission Control) to transmit data via various types of media. TCP/IP is not a single networking protocol. It is a suite of protocols named after the two most important protocols or layers within it TCP and IP. As with any form of communication, two things are needed: a message to transmit and the me to reliably transmit the message.
![]()
Question 3.
Write a note on Hotspot Internet service?
Answer:
Hotspots are sites that offer Internet access over a Wireless Local Area Network (WLAN) by way of a router that then connects to an Internet service provider.
Hotspots utilize Wi-Fi technology, which allows electronic devices to connect to the Internet or exchange data wirelessly through radio waves. Hotspots can be phone-based or free-standing, commercial or free to the public.
Question 4.
Differentiate Data Card and Dongles?
Answer:
Data card:
It is a removable electronic card which is used for storing data. Types of datacard are –
- Expansion Card
- Memory Card or Flash Card
- Identification Card
Dongle:
Refers to any removable component used for enabling extra security. USB Dongles can be divided into
- Wi-Fi Dongles
- BlueTooth Dongle
- Memory Dongle
![]()
Question 5.
Write a note on two access methods of connecting to Internet?
Answer:
There are two access methods Direct and Indirect and these can be either fixed or mobile.
Indirect Access:
This is most common method used in home and office networks.
The device (Eg: Computer) connects to a network using Ethernet or Wi-Fi and the network connects to the Internet using Asymmetric Digital Subscriber Line ADSL (cable or fibre.)
Direct Access:
This is most common method used when travelling. The device (Eg: smart phone) connects directly to the Internet using 3G/4G mobile networks or public Wi-Fi.
![]()
Question 6.
Differentiate browser and a search engine with suitable examples?
Answer:
Browser:
- A browser is used to access website and web pages.
- A browser is used to access the Internet.
- Eg: Internet explorer, Chrome and Firefox.
Search Engine:
- A search engine is used to search for particular information.
- A search engine to search for information on the World Wide Web.
- Eg: Yahoo, Lycos, Altavista and Google.
Question 7.
Differentiate Website and Webpage?
Answer:
Webpage:
- Consists of a Single document displayed by a browser.
- Shares a unique domain name.
- Makes up a website.
- Static web pages directly run on the browser and do not require any server side application program.
- Static Web pages are easy to develop.
Website:
- A collection of multiple documents displayable by a browser.
- Has its own unique domain name .
- Contains one or more webpages.
- Dynamic web pages runs on the server side application programs and displays the results.
- Dynamic web page development requires programming skills.
![]()
Question 9.
Write a note on W3C?
Answer:
W3C stands for “World Wide Web Consortium.” The W3C is an international community that includes a full-time staff, industry experts, and several member organizations. These groups work together to develop standards for the World Wide Web.
It is made up of several hundred member organizations from a variety of related IT industries. W3C sets standards for the World Wide Web (WWW) to facilitate better communication ability and cooperation among all web stakeholders.
Question 10.
What are Advantages of e-mail?
Answer:
(i) Free delivery:
Sending an e-mail is virtually free, outside the cost of Internet service. There is no need to buy a postage stamp to send a letter.
(ii) Global delivery:
E-mail can be sent to nearly anywhere around the world, to any country.
(iii) Instant delivery:
An e-mail can be instantly sent and received by the recipient over the Internet.
(iv) File attachment:
An e-mail can include one or more file attachments, allowing a person to send documents, pictures, or other files with an e-mail.
IV. Answer To The Following Questions
Question 1.
Compare the different geographical types of Network?
Answer:
(I) LAN -Local Area Network:
1. Range:
Upto 10 Km.
2. Location:
Refers to same office, same building, same company and in same schools.
3. Speed:
Upto 10-100 Mbps.
4. Advantages:
Low Cost, Resource Sharing, Security.
5. Disadvantages:
Area Covered Limited. When number of nodes increases, performance decreases.
(II) MAN – Metropolitan Area Network:
1. Range:
10 to 15 Miles.
2. Location:
MAN is a network designed to extend over an entire city.
3. Speed:
Upto 5-10 Mbps.
4. Advantages:
Wider than LAN.
5. Disadvantages:
Data rate is slow compared to LAN and Cost is higher than LAN.
(III) WAN – Wide Area Network:
Range: Above 1000 Kms.
1. Location:
It Span entire countries and continents.
2. Speed:
Upto 256 Kbps to 2 Mbps. Advantages: Large geographical Area.
3. Disadvantages:
Complicated and Complex, High Cost, Requires high Performance Devices, Low security, Cost is higher than LAN.
(IV) PAN – Personal Area Network:
1. Range:
Upto 100 meters.
2. Location:
Used for shorter distance, controlled by a single person within a single building.
3. Speed:
Upto 250 Kbps.
4. Advantages:
Efficient, Cost effective and convenient. Controlled by a single person. Hotspot may connect upto 8 devices.
5. Disadvantages:
Shorter distance upto 10 meters only. Data rate is low compared to other network.
(V) CAN – Campus Area Network:
1. Range:
Upto 5 Kms.
2. Location:
Larger than LAN, but smaller than MAN. University, school or small business, enterprise.
3. Speed:
40 Kb/s to 1 MB/s
4. Advantages:
Cost effective,Wired or Wireless Network, High Bandwidth Multi-departmental Network access.
5. Disadvantages:
Difficult to manage
(VI) WLAN – Wireless Local Area Network:
1. Range:
Upto 50 Kms
2. Location:
Ranges from a single room to an entire campus: Uses Wi-Fi or Bluetooth, Radio waves.
3. Speed:
1 Mbps to 54 Mbps
4. Advantages:
Portable Installation is quick and easy.
5. Disadvantages:
Low Bandwidth due to interference.
![]()
Question 2.
Explain any five types of Internet services?
Answer:
(i) Wireless:
Radio frequency bands are used in place of telephone or cable networks. One of the greatest advantages of wireless Internet connections is the “always-on” connection that can be accessed from any location that falls within network coverage. Wireless connections are made possible through the use of a modem, which picks up Internet signals and sends them to other devices.
(ii) Mobile:
Many cell phone and smartphone providers offer voice plAnswer:w ith Internet access. Mobile Internet connections provide good speeds and allow you to access the Internet.
(iii) Hotspots:
Hotspots are sites that offer Internet access over a Wifeless Local Area Network (WLAN) by way of a router that then connects to an Internet service provider.
Hotspots utilize Wi-Fi technology, which allows electronic devices to connect to the Internet or exchange data wirelessly through radio waves. Hotspots can be phone-based or free-standing, commercial or free to the public.
(iv) Broadband:
This high-speed Internet connection is provided through either cable or telephone companies. One of the fastest options available, broadband Internet uses multiple data channels to send large quantities of information.
The term broadband is shorthand for broad bandwidth. Broadband Internet connections such as DSL and cable are considered high-bandwidth connections. Although many DSL connections can be considered broadband, not all broadband connections are DSL.
(v) DSL:
DSL, which stands for Digital Subscriber Line, uses existing 2-wire copper telephone line connected to one’s home. So service is delivered at the same time as landline telephone service. Customers can still place calls while surfing the Internet.
![]()
Question 3.
Explain any five Internet applications with suitable examples?
Answer:
(i) Internet telephony:
Internet telephony (Eg: Skype) is another common communications service made possible by the creation of the Internet. VoIP stands for Voice-over-Internet Protocol, referring to the protocol that underlies all Internet communication.
(ii) Job search:
Nowadays, many people search for their jobs online as it is quicker and there is a larger variety of job vacancies present. People can publish resume online for prospective job. Some of the web sites providing this service are naukri.com, monster.com, summer iob. com, recruitment india ofii etc…
(iii) Online Shopping:
The Internet has also facilitated the introduction of a new market concept consisting of virtual shops. They provide information about products or services for sale through www servers.
Using the Internet services customers can submit specific product queries and request specific sales quotes. For example amazon.com is a www based bookshop on the Internet where information on all types of international books can be found and books can be ordered online.
(iv) Stock market updates:
Selling or buying shares sitting on computer through Internet. Several websites like ndtvprofit.com, moneypore.com, provide information regarding investment.
(v) Travel:
One can use Internet to gather information about various tourist place. It can be used for booking Holiday tours, hotels, train, bus, flights and cabs. Some of the websites providing this service are goibibo.com, makemytrip.com, olacabs. com.
![]()
Question 4.
Write a note on any five Internet browsers other than that given in the book?
Answer:
(i) Microsoft Edge:
The faster, safer way to get things done on the web. Edge go from your mobile device or tablet.
(ii) Opera:
Opera browser for windows with a built-in ad blocker and VPN. Our free web browser for windows brings you more speed and privacy.
(iii) Vivaldi:
We use cookies to offer you a better browsing experience and analyze site traffic. If you continue to use this site, you consent to our use of cookies.
(iv) Comodo Dragon:
It helps you stay safe and secure. Provides unsurpassed speed. Friendly user interface, customized plug-ins and add-ons. No more crashes or frozen screens.
(v) Brave:
Brave is on a mission to fix the Web. Much more than a browser, Brave is a new way of thinking about how the Web works. No more data changes to download unwanted content.
![]()
Question 5.
Classify and explain any five e-commerce parties with suitable examples?
Answer:
(i) Business to Consumer (B2C):
Transactions happen between businesses and consumers. In B2C e-commerce, businesses are the ones selling products or services to end-users (i.e., consumers).
(ii) Business to Business (B2B):
As its name states, B2B e-commerce pertains to transactions conducted between two businesses. Any company whose customers are other businesses operate on a B2B model. .
(iii) Consumer to Business (C2B):
Consumer to business e-commerce happens when a consumer sells or contributes monetary value to a business. Many crowdsourcing campaigns fall under C2B e-commerce.
(iv) Consumer to Consumer (C2C):
As you might have guessed, C2C e-commerce happens when something is bought and sold between two consumers. C2C commonly takes place on online market places such as e-Bay, in which one individual sells a product or service to another.
(v) Government to Business (G2B):
G2C transactions take place when a company pays for government goods, services, or fees online. Examples could be a business paying for taxes using the Internet.
Question 6.
Explain the different types of interactions in e-governance?
Answer:
(i) G2G (Government to Government):
When the exchange of information and services is within the periphery of the government, is termed as G2G interaction. This Can be both horizontal, i.e., among vanous government entities and vertical, i.e., between national, state and local government entities and within different levels of the entity.
(ii) G2C (Government to Citizen):
The interaction amidst the government and general public is G2C interaction. Here an interface is set up between government and citizens, which enables citizens to get access to wide variety of public services. The citizens has the freedom to share their views and grievances on government policies anytime, anywhere.
(iii) G2B (Government to Business):
In this case, the e-govemance helps the business class to interact with the government seamlessly. It aims at eliminating red-tapism, saving time, cost and establish transparency in the business environment, while interacting with government.
(iv) G2E (Government to Employees):
The government of any country is the biggest employer and so it also deals with employees on a regular basis, as other employers do. ICT helps in making the interaction between government and employees fast and efficient, along with raising their level of satisfaction by providing perquisites and add-on benefits.
E-govemance has a great role to play, that improves and supports all tasks performed by the government department and agencies, because it simplifies the task on the one hand and increases the quality of work on the other.
Samacheer Kalvi 11th Computer Applications Introduction to Internet and Email Additional Questions and Answers
I. Choose The Correct Answer
Question 1.
Which type of Network is covered within a building or company?
(a) LAN
(b) MAN
(c) WAN
(d) PAN
Answer:
(a) LAN
![]()
Question 2.
Which Network is covered over entire city?
(a) LAN
(b) MAN
(c) WAN
(d) PAN
Answer:
(b) MAN
Question 3.
The Network is span entire countries and continents:
(a) LAN
(b) MAN
(c) WAN
(d) PAN
Answer:
(c) WAN
![]()
Question 4.
Which network is controlled by a single person within a single building?
(a) LAN
(b) MAN
(c) WAN
(d) PAN
Answer:
(d) PAN
Question 5.
Which network is used for High Bandwidth Multi-departmental wired network?
(a) MAN
(b) CAN
(c) PAN
(d) WAN
Answer:
(b) CAN
Question 6.
Which network is used for wi-fi or Bluetooth?
(a) WLAN
(b) LAN
(c) MAN
(d) WAN
Answer:
(a) WLAN
![]()
Question 7.
The protocol by used Internet:
(a) TCP/IP
(b) http
(c) HTT
(d) TC/IP
Answer:
(a) TCP/IP
Question 8.
A private network that uses Internet Technologies:
(a) Internet
(b) Network
(c) Extranet
(d) LAN
Answer:
(c) Extranet
Question 9.
Who is called Father of the Internet?
(a) Vinton Gray Cerf
(b) Tim Berners-Lee
(c) Charless Babbage
(d) William Cerf
Answer:
(a) Vinton Gray Cerf
![]()
Question 10.
Who was also involved in the formation of ICANN?
(a) Vinton Gray Cerf
(b) Tim Berners-Lee
(c) Bob Kahn
(d) William Cerf
Answer:
(a) Vinton Gray Cerf
Question 11.
Which name is used to online identity and can be access by the web browser when connected the Internet?
(a) E-mail
(b) Domain name
(c) FTP
(d) Profocol
Answer:
(b) Domain name
![]()
Question 12.
The Generic domain name system of Government Institutions:
(a) .com
(b) .gov.
(c) -org
(d) .edu
Answer:
(b) .gov.
Question 13.
The Generic domain nam? system of Educational Institution:
(a) .com
(b) .gov
(c) .org
(d) .edu
Answer:
(d) .edu
![]()
Question 14.
The heart of intranets and the Internet is called as:
(a) DNS
(b) IP
(c) TCP
(d) FTP
Answer:
(a) DNS
Question 15.
Which is used as Internet address information?
(a) IP
(b) DNS
(c) TC
(d) FTP
Answer:
(a) IP
Question 16.
Which system is used to deliver mail and other information from computer to computer?
(a) IP
(b) DNS
(c) TC
(d) FTP
Answer:
(b) DNS
![]()
Question 17.
The country level domain name system in India is:
(a) . in
(b) .us
(c) -sg
(d) .ru
Answer:
(a) . in
Question 18.
TJie country level domain name system in USA is:
(a) .in
(b) .us
(c) sg
(d) .ru
Answer:
(b) .us
Question 19.
The country level domain name system in Singapore is:
(a) .in
(b) .us
(c) .sg
(d) .ru
Answer:
(c) .sg
![]()
Question 20.
How many parts are IP address?
(a) 2
(b) 3
(c) 4
(d) 5
Answer:
(c) 4
Question 21.
IP address is separated by:
(a) dots
(b) comma
(c) ‘semi-colon’
(d) colon
Answer:
(a) dots
Question 22.
URL abbreviation is:
(a) Uniform Resource Locator
(b) Uniform Reserve Locator
(c) Uniform Resistance Locator
(d) Uniform Read Locator
Answer:
(a) Uniform Resource Locator
![]()
Question 23.
ICANN stands for:
(a) Internet Corporation for Assigned Names and Numbers
(b) Intranet Corporation for Assigned Names and Numbers
(c) Internet Corporation for Assigned Names and Natives
(d) Internet Community for Assigned Names and Numbers
Answer:
(a) Internet Corporation for Assigned Names and Numbers
Question 24.
ICANN head quarters is:
(a) Los Angeles
(b) New York
(c) Playa Vista
(d) San Francisco
Answer:
(c) Playa Vista
Question 25.
W3C stands for:
(a) World Wide Work Consortium
(b) World Wide Web Consortium
(c) World Wide Web Connector
(d) World Wide Web Council
Answer:
(b) World Wide Web Consortium
![]()
Question 26.
What is the greatest advantage of Wireless Internet Connection?
(a) Fast
(b) Easy way
(c) Always-on
(d) Accessed
Answer:
(c) Always-on
Question 27.
Which device is used to pick up and send Internet signals?
(a) Modem
(b) Cable
(c) Telephone
(d) Wireless
Answer:
(a) Modem
Question 28.
Which device provides good speed and allow you to access the Internet anywhere?
(a) Cellphone
(b) Desktop computer
(c) Removable device
(d) None
Answer:
(a) Cellphone
![]()
Question 29.
Which technology allows to connect the Internet or exchanges data wirelessly through radio waves?
(a) Wi-Fi
(b) LAN
(c) WAN
(d) PAN
Answer:
(a) Wi-Fi
Question 30.
The term broadband is shorthand for:
(a) broad bandwidth
(b) broad banding
(c) broad bandlength
(d) none
Answer:
(a) broad bandwidth
Question 31.
DSL stands for:
(a) Digital Subscriber Line
(b) Digital Super Line
(c) Digital Secondary Line
(d) Digital Source Line
Answer:
(a) Digital Subscriber Line
![]()
Question 32.
Which network allows user to send data, voice and video content?
(a) Wireless
(b) ISDN
(c) WLAN
(d) DSL
Answer:
(b) ISDN
Question 33.
ISDN stands for:
(a) Integrated Services Digital Network
(b) International Services Digital Network
(c) International Source Digital Network
(d) Integrated Services Digital Node
Answer:
(a) Integrated Services Digital Network
Question 34.
ADSL stands for:
(a) Asymmetric Digital Subscriber Line
(b) Assume Digital Subscriber Line
(c) Arrange Digital Subscriber Line
(d) Asymmetric Digital Secondary Line
Answer:
(a) Asymmetric Digital Subscriber Line
![]()
Question 35.
VoIP stands for:
(a) Value-over Internet Protocol
(b) Voiee-over Internet Protocol
(c) Volume-over Internet Protocol
(d) Visual-over Internet Protocol
Answer:
(b) Voiee-over Internet Protocol
Question 36.
Which system is sending message over the phone and they can listen to their message later?
(a) Video conferencing
(b) Voice mail
(c) Chatting
(d) e-Banking
Answer:
(b) Voice mail
Question 29.
Which technology allows to connect the Internet or exchanges data wirelessly through radio waves?
(a) Wi-Fi
(b) LAN
(c) WAN
(d) PAN
Answer:
(a) Wi-Fi
![]()
Question 30.
The term broadband is shorthand for:
(a) broad bandwidth
(b) broad banding
(c) broad bandlength
(d) none
Answer:
(a) broad bandwidth
Question 31.
DSL stands for:
(a) Digital Subscriber Line
(b) Digital Super Line
(c) Digital Secondary Line
(d) Digital Source Line
Answer:
(a) Digital Subscriber Line
Question 32.
Which network allows user to send data, voice and video content?
(a) Wireless
(b) ISDN
(c) WLAN
(d) DSL
Answer:
(b) ISDN
![]()
Question 33.
ISDN stands for:
(a) Integrated Services Digital Network
(b) International Services Digital Network
(c) International Source Digital Network
(d) Integrated Services Digital Node
Answer:
(a) Integrated Services Digital Network
Question 34.
ADSL stands for:
(a) Asymmetric Digital Subscriber Line
(b) Assume Digital Subscriber Line
(c) Arrange Digital Subscriber Line
(d) Asymmetric Digital Secondary Line
Answer:
(a) Asymmetric Digital Subscriber Line
![]()
Question 35.
VoIP stands for:
(a) Value-over Internet Protocol
(b) Voiee-over Internet Protocol
(c) Volume-over Internet Protocol
(d) Visual-over Internet Protocol
Answer:
(b) Voiee-over Internet Protocol
Question 36.
Which system is sending message over the phone and they can listen to their message later?
(a) Video conferencing
(b) Voice mail
(c) Chatting
(d) e-Banking
Answer:
(b) Voice mail
Question 37.
Which system is taking in Internet can be on going or scheduled for a particular time or duration?
(a) Video conferencing
(b) Voice mail
(c) Chatting
(d) e-Banking
Answer:
(c) Chatting
![]()
Question 38.
Which system is known as Internet banking?
(a) Video conferencing
(b) Voice mail
(c) Chatting
(d) e-Banking
Answer:
(d) e-Banking
Question 39.
The system is utilizing electronic technologies to access educational curriculam outside of a traditional class room:
(a) video mail
(b) c-learning
(c) chatting
(d) e-banking
Answer:
(b) c-learning
![]()
Question 40.
Who was sent a first e-mail?
(a) Ray Tomlinson
(b) Bob Kahn
(c) Vinton Gray Cerf
(d) Tim Berners-Lee
Answer:
(a) Ray Tomlinson
Question 41.
What is the use of compose button in die mail window?
(a) Writting e-mail content
(b) Searching files
(c) Copy the file
(d) Modifing the file
Answer:
(a) Writting e-mail content
![]()
Question 42.
Which software is created by cyber criminals to spy on their victims?
(a) Virus
(b) Malicious spyware
(c) Spam
(d) Phishing
Answer:
(b) Malicious spyware
Question 43.
Which software program can copy itself from one computer to another without human Interaction?
(a) Malware
(b) Botnet
(c) Computer worm
(d) Spam
Answer:
(c) Computer worm
![]()
Question 44.
The group of computers connected to the Internet that have been compromised by a hacker using a computer virus:
(a) malware
(b) botnet
(c) computer worm
(d) spam
Answer:
(b) botnet
Question 45.
Which is described as unwanted messages in your e-mail box and is a nuisance as it can . clutter your mail box?
(a) Malware
(b) Botnet
(c) Computer worm
(d) Spam
Answer:
(b) Botnet
Question 46.
The scams are fraudulent attempts by cyber criminals to obtain private information:
(a) phishing
(b) malware
(c) botnet
(d) spam
Answer:
(a) phishing
![]()
Question 47.
Which tools are used to obtain administrator- level access to a computer or a network of computers?
(a) Phishing
(b) Malware
(c) Root kit
(d) Spam
Answer:
(c) Root kit
Question 48.
Browsing for information on the Internet is called:
(a) surfing
(b) phishing
(c) spam
(d) worm
Answer:
(a) surfing
Question 49.
To browse the Internet, a software is called:
(a) Botnet
(b) Spam
(c) Web browser
(d) Phishing
Answer:
(c) Web browser
![]()
Question 50.
Google Inc. was developed for familiar web browser is:
(a) chrome
(b) firefox
(c) safari
(d) vivaldi
Answer:
(a) chrome
Question 51.
Safari is a web browser, who was developed by:
(a) Google Inc.
(b) Mozilla foundation
(c) Apple Inc
(d) Microsoft Corp
Answer:
(c) Apple Inc
Question 52.
A collection of webpages is called:
(a) website
(b) e-mail
(c) web service
(d) home page
Answer:
(a) website
![]()
Question 53.
Every web page has a unique address called the:
(a) URL
(b) ICANN
(c) CC
(d) BCC
Answer:
(a) URL
Question 54.
Which type of websites remain the same whenever it is visited?
(a) Static
(b) Dynamic
(c) Both (a) & (b)
(d) URL
Answer:
(a) Static
![]()
Question 55.
Which website content and layout may change during run time?
(a) Static
(b) Dynamic
(c) Both (a) & (b)
(d) URL
Answer:
(b) Dynamic
Question 56.
The activity of buying or selling of products on online services or over the Internet:
(a) e-mail
(b) e-commerce:
(c) e-leaming
(d) e-govemance
Answer:
(b) e-commerce:
Question 57.
Which term is used by transactions happen between business and consumers?
(a) B2C
(b) B2B
(c) C2B
(d) C2C
Answer:
(a) B2C
![]()
Question 58.
Which term is used to pertain transactions conducted between two business?
(a) B2C
(b) B2B
(c) C2B
(d) C2C
Answer:
(b) B2B
Question 59.
The application of information and communication technology for delivering government services are:
(a) G2C
(b) e-govemance
(c) e-commerce
(d) e-leaming
Answer:
(b) e-govemance
Question 60.
A great role to play, that improves and supports all tasks performed by the government department and agencies are:
(a) e-commerce
(b) e-govemance
(c) e-leaming
(d) e-mail
Answer:
(b) e-governance
![]()
Question 61.
Which month can be celebrated ‘Safer Internet Day’of every year?
(a) January
(b) February
(c) March
(d) May
Answer:
(b) February
Question 62.
Which is a software managing technique through which programs that are suspected to be infected with a virus can be run?
(a) Sandboxing
(b) Spam
(c) Phishing
(d) Botnet
Answer:
(a) Sandboxing
Question 63.
IoT – means:
(a) Internet of Things
(b) International of Things
(c) Internet of Timings
(d) Internet of Teachings
Answer:
(a) Internet of Things
![]()
Question 64.
USB, Wi-Fi are removable component and it refers:
(a) device
(b) dongle
(c) electronic parts
(d) electronic governance
Answer:
(b) dongle
II. Answer To The Following Questions
Question 1.
Any two advantages for necessity of using Internet in commerce?
Answer:
The cost, time and effort involved in transferring data was much higher without , networks. So networks, decrease cost, time, and effort and thereby increase productivity. They also help in resource optimization by helping to share resources.
Question 2.
What are the disadvantages of using WAN?
Answer:
- Complicated and complex.
- High cost.
- Requires high performance devices.
- Low security.
- Cost higher than LAN.
Question 3.
What are the advantages of using PAN network?
Answer:
- Efficient.
- Cost effective and convenient.
- Controlled by a single person.
- Hotspot may connect upto 8 devices.
![]()
Question 4.
Write any four popular social sharing tools.
Answer:
Question 5.
What is a domain name?
Answer:
It is a name or an identity which become a online identity and can be accessed by the web browser when connected to Internet.
Question 6.
Write any four country level domain name?
Ans
Description:
- India
- Australia
- United States of America
- Japan
Country level Domain Name:
- .in
- .au
- .us
- .jp
![]()
Question 7.
what is an URL?
Answer:
A URL is an address that shows where a particular page can be found on the World Wide Web. URL is an abbreviation for ‘Uniform Resource Locator (URL)’.
Question 8.
Who governs the Internet?
Answer:
The Internet as a whole does not have a single controller. But the Internet. society, which is a voluntary membership organization, takes the responsibility to promote global information exchange through the Internet technology.
Question 9.
What is a ISDN?
Answer:
ISDN (Integrated Services Digital Network) allows users to send data, voice and video content over digital telephone lines or standard telephone wires. The installation of an ISDN adapter is required at both ends of the transmission – on the part of the user as well as the Internet access provider.
Question 10.
What is an Indirect Access in Internet?
Answer:
This is most common method used in home and office networks.
The device (Eg: Computer) connects to a network using Ethernet or Wi-Fi and the network connects to the Internet using Asymmetric Digital Subscriber Line ADSL, (cable or fibre.)
![]()
Question 11.
What is an Direct Access in Internet?
Answer:
This is most common method used when travelling. The device (Eg: Smart phone) connects directly to the Internet using 3G/4G mobile networks or public Wi-Fi.
Question 12.
Give some most popular search engines?
Answer:
Yahoo, Lycos, Altavista, Hotbot, Google and Askjeeves are the most popular search engines.
Question 13.
What is the purpose of voicemail in Internet?
Answer:
Voicemail is a system of sending messages over the phone. Calls are answered by a machine which connects you to the person you want to leave a message for, and they can listen to their messages later.
Question 14.
What is sent in an e-mail?
Answer:
Text messages being sent over e-mail, it is also possible to attach a file or other data in , an e-mail. For example, an attachment could be a picture, PDF,word processor document, or any file stored on the computer.
![]()
Question 15.
What is a computer virus?
Answer:
A computer virus is a small piece of software that can spread from one infected computer to another. The virus could corrupt, steal, or delete data on your computer-even erasing everything on your hard drive. A virus could also use other programs like your e-mail program to spread itself to other computers.
Question 16.
What is a malicious software?
Answer:
Malware is short for “malicious software.” Malware is used to mean a “variety of forms of hostile, intrusive, or annoying software or program code.” Malware could be computer viruses, worms, Trojan horses, dishonest spyware, and malicious rootkits all of which are .defined below.
Question 17.
What is an Trojan horse software?
Answer:
Users can infect their computers with Trojan horse software simply by downloading an application they thought was legitimate but was in fact malicious.
Once it enters inside the computer, a Trojan horse can do anything from recording your passwords by logging its keystrokes, hijacking your webcam to watch and record every movement.
![]()
Question 18.
What is a Botnet?
Answer:
A botnet is a group of computers connected to the Internet that have been compromised by a hacker using a computer virus or Trojan horse. An individual computer in the group is known as a “zombie” computer.
Question 19.
What is a spam?
Answer:
Spam in the security context is primarily used to describe e-mail spam. Unwanted messages in your e-mail inbox. Spam, or electronic junk mail, is a nuisance as it can clutter your mailbox as well as potentially take up space on your mail server.
However, spam messages can contain links that when clicked on could go to a website that installs malicious software onto your computer.
Question 20.
What is a Rootkit?
Answer:
A root kit is a collection of tools that are used to obtain administrator-level access to a computer or a network of computers. A root kit could be installed on your computer by a cyber criminal exploiting a vulnerability or security hole in a legitimate application on your PC and may contain spyware that monitors and records keystrokes.
![]()
Question 21.
What is a web page?
Answer:
A webpage is a page of a Website. A web that page can be copied and or send to a friend for review whereas websites are collections of multiple page that must be navigated to view other content.
Question 22.
What is an commerce?
Answer:
e-commerce is the activity of buying or selling of products on online services or over the Internet. Electronic commerce draws on technologies such as mobile commerce, electronic funds transfer, supply chain management, Internet marketing, online transaction processing, electronic data interchange (EDI), inventory management systems, and automated data collection systems.
Question 23.
What is a purpose of sandboxing software?
Answer:
Sand boxing is a software managing technique through which programs that are suspected to be infected with a virus can be run. The programs are run in a separated memory area and therefore cannot damage the operating systems.
Question 24.
What is mean by Hotspots?
Answer:
Hotspots are sites that offer Internet access over Wireless Local Network (WLAN) by way of a router that then connects to an Internet service provider.
![]()
Question 25.
What is a Internet telephony?
Answer:
Internet telephony (Eg: Skype) is another common communications service made possible by the creation of the Internet. VoIP stands for Voice-over-Internet Protocol.
Question 26.
What is a Dongle?
Answer:
Dongle refers to removable component used for enabling software protection.
Eg: USB, Wi-Fi.
![]()
Question 27.
What are the ways to lookfor the information on the web?
Answer:
There are two ways to look for the information on the web.
- If the URL of the website is known, enter it on the address bar.
- If is the URL is not known, then ‘Search Engines’ will help us to get the information.
III. Answer To The Following Questions
Question 1.
Differentiate an extranet and an intranet?
Answer:
Extranet:
An extranet is a private network that uses Internet technology and the public telecommunication system to securely share part of a business’s information or operations with Suppliers, vendors, partners, customers, or other businesses.
Intranet:
An Intranet is a website used by organizations to provide a place where employees can access company information (Eg: policies, procedures, staff, directory, department info), tools (quick links to common apps, forms etc…) and (collaborate to social sharing tools similar facebook).
![]()
Question 2.
What are the services available from Internet?
Answer:
- Email.
- Web-enabled audio/video conferencing services.
- Online movies and gaming.
- Data transfer/file-sharing, often through File Transfer Protocol (FTP).
- Instant messaging.
- Internet forums.
- Social networking.
- Online shopping.
- Financial services.
Question 3.
What is the purpose of DNS?
Answer:
The heart of intranets and the Internet is called as the Domain Name System(DNS), the way computers can contact each other and do things such as exchange electronic mail or display Web pages. The Internet Protocol (IP) uses this Internet address information and the DNS to deliver mail and other information from computer to computer.
![]()
Question 4.
What is meant by Broadband?
Answer:
High-speed Internet connection is provided through either cable or telephone companies. One of the fastest options available, broadband Internet uses multiple data channels to send large quantities of information.
The term broadband is shorthand for broad bandwidth. Broadband Internet connections such as DSL and cable are considered high- bandwidth connections. Although many DSL connections can be considered broadband, not all broadband connections are DSL.
Question 5.
What is chatting on the Internet?
Answer:
On the Internet, chatting is talking to other people who are using the Internet at the same time you are. Usually, this “talking” is the exchange of typed-in messages and a group of users who take part from anywhere on the Internet. Chats can be ongoing or scheduled for a particular time and duration.
Most chats are focused on a particular topic of interest and some involve guest experts or famous people who “talk” to anyone joining the chat. Transcripts of a chat can be archived for later reference.
![]()
Question 6.
What is online banking services?
Answer:
e-banking (Online banking), also known as Internet banking, it is an electronic payment system that enables customers of a bank or other financial institution to conduct a range of financial transactions through the financial institution’s website.
The online banking system will typically connect to or be part of the core banking system operated by a bank and is in contrast to branch banking which was the traditional way customers accessed banking services.
Question 7.
What is a e-learning?
Answer:
e-Leaming are courses that are specifically delivered via the Internet to somewhere other than the classroom where the professor is teaching. It is not a course delivered via a DVD or CD-ROM, video tape or over a television channel. e-leaming is utilizing electronic technologies to access educational curriculum outside of a traditional classroom. It is a program delivered completely online.
E-leaming is interactive in that you can also communicate with teachers, professors or other students in a class. Sometimes it is delivered live, where you can “electronically” raise your hand and interact in real time and sometimes it is a lecture that is prerecorded. There is always a teacher/professor interacting/ communicating, grading participation, giving assignments and conducting tests.
![]()
Question 8.
What is a Malicious spyware software?
Answer:
Malicious spyware:
Malicious spyware is used to describe the Trojan application that was created by cyber criminals to on their victims. An example would be key logger software that records a victim’s every keystroke on his or her keyboard.
The recorded information is periodically sent back to the originating cyber criminal over the Internet. Key logging software is widely available and is marketed to parents or businesses that want to monitor their kid’s or employee’s Internet usage.
Question 9.
What is a computer worm software?
Answer:
A computer worm is a software program that can copy itself from one computer to another, without human interaction. Worms can replicate in great volume and with great speed. For example, a worm can send copies of itself to every contact in your email address book and then send itself to all the contacts in your contact’s address books.
Because of their speed of infection, worms often gain notoriety overnight infecting computers across the globe as quickly as victims around the world and switch them on to open their e-mail.
![]()
Question 10.
What are the familiar Internet Browsers?
Answer:
(i) Google-Chrome:
It is a freeware familiar web browser developed by Google Inc, It is best for its speed, simplicity, security, privacy and customization features. Google Chrome supports on Android 4.0 or higher, iOS 6.0 or higher, Mac OSX 10.6 or higher and Windows (XP sp2 or higher) and Linux system.
(ii) Mozila Firefox:
It is a free and open source web browser developed by Mozilla Foundation and Mozilla Corporation. Firefox is default browser in Ubuntu. It supports Windows, Mac OS X, Linux and Android system.
(iii) Internet Explorer:
It is commonly known as Microsoft Internet Explorer or Windows Internet Explorer is the first or default browser for a Windows PC. It is developed by Microsoft.
(iv) Safari:
It is a web browser developed by Apple Inc. and comes with OS X and iOS. Some version of safari browser also supports in Windows Operating System. Exclusively used in Apple Mac system.
![]()
Question 11.
What is the Internet of Things (loT)?
Answer:
The Internet of Things (IoT) is the network of physical devices, such as vehicles, home appliances, and other items embedded with electronics, software, sensors, actuators and connectivity which enables these things to connect and exchanges data creating opportunities for more direct integration of the physical world into computer – based systems, resulting in effficiency improvements, economic benefits, and reduced human exertions.
IV. Answer To The Following Questions
Question 1.
Write the any five Generic Domain Name?
Answer:
Generic Domain Name:
- .com
- .gov
- .org
- .net
- .edu
Description:
- Commercial Organisation
- Government institution
- Non-profit Organisation
- Network Support Group
- Educational Institution
![]()
Question 2.
Write the steps of structure of e-mail?
Answer:
Click the Compose button and then writing an e-mail contents.
When sending an e-mail message, several fields are required to be filled:
- The To field is where you type the e-mail address of the person who is the recipient of your message.
- The From field should contain your e-mail address.
- If you are replying to a message, the To and From fields are automatically filled out; if it’s a new message, you’ll need to enter them manually.
- The Subject should consist of a few words describing the e-mail’s contents. The Subject lets the recipient see what the e-mail is about, without opening and reading the full e-mail. This field is optional.
- The CC (Carbon Copy) field allows you to specify recipients who are not direct addresses (listed in the “To” field). This field is optional.
- The BCC (Blind Carbon Copy) field is similar to CC, except the recipients are secret. Each BCC recipient will receive the e-mail, but will not see who else received a copy. The addresses (anyone listed in the “To” field) remain visible to all recipients. This field is optional.
- Finally, the Message Body is the location you type your main message. It often contains your signature at the bottom; similar to a hand-written letter.
Question 3.
Write the any five points do’s and don’t of safe surfing on Internet?
Answer:
(i) Don’tgiveoutyourpersonal information:
Don’t put personal details such as your home address, telephone numbers or parent’s work address online as cybercriminals can use this information to create a fake profile with your details.
(ii) What goes online, stays online:
Use privacy settings to make sure only your friends and family can see photos you post. Avoid posting holiday plAnswer:as criminals have been known to track your movements.
(iii) Check your security and privacy settings:
Make sure your social network privacy settings are secured so only your friends can see your personal information and use your privacy settings to restrict who can see your posts, videos and photos.
(iv) Password safety:
Sharing your password with your parents is a sensible idea, but avoid sharing your password with your friends, even if they promise they won’t tell anyone! Also, when setting your password, make sure it isn’t something people may guess such as your pet’s name. Use a mixture of letters, numbers and upper and lower case characters.
(v) Always protect your mobile device:
Make sure your mobile phone is pin-protected. So all your personal information stored on it is safe. Download a security app which allows you to remotely wipe any personal data, should your mobile be lost or stolen.